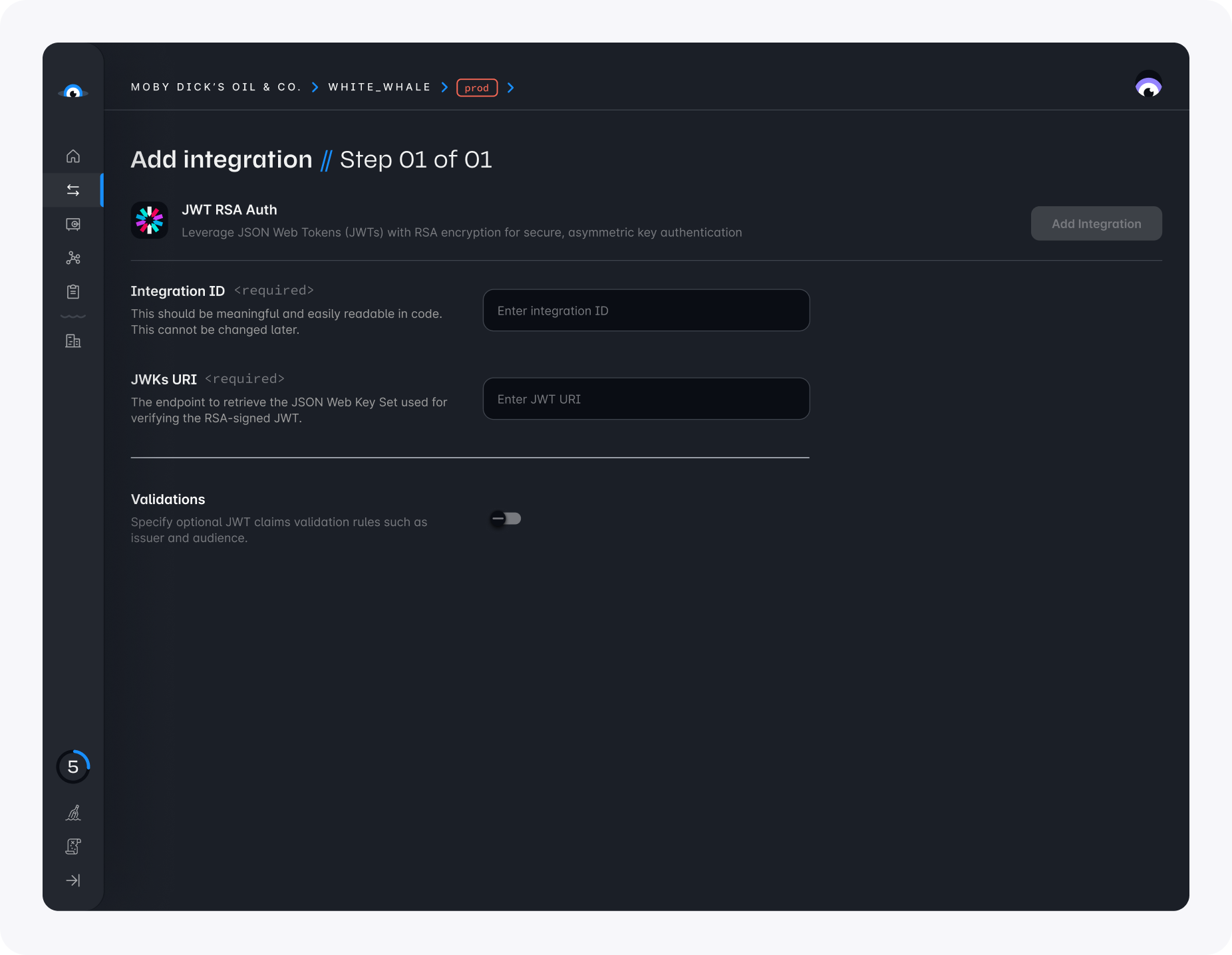
JWT RSA
The JWT RSA integration allows Squid to integrate with any RSA signed JWTs, as long as public signing keys are publicly available.
In some cases, you may be using your own custom authentication tokens, instead of receiving tokens from an Auth provider. These tokens are most commonly issued as JWTs, which can be signed using a few different signing algorithms. This integration supports any JWTs that have been signed with public/private key pair using the RSA algorithm.
When creating a JWT RSA integration, you will need to provide the following information:
- JWKS URI: The URI to fetch the publicly available JSON Web Keys Set, which can be used to verify the token.
- Validations: Optional checks to verify who issued the token, and the token's intended audience.
- Issuer: Verifies that the issuer of the token (
iss) matches the specified value. - Audience: Verifies that the audience of the token (
aud) matches the specified value.
How it works
To verify that the JWT passed to Squid is valid, Squid will fetch the public key associated with the token. This is fetched through the JWKS URI, which must be passed when creating a JWT RSA integration.
Using the integration
Once you've created an integration, you can use the Squid Client SDK pass the Access Token through to Squid:
squid.setAuthProvider({
integrationId: 'AUTH_INTEGRATION_ID',
getToken: () => 'USER_AUTH_ID_TOKEN',
});
This will automatically populate the user's authentication information for use in your backend functions:
@secureCollection('users', 'read')
secureUsersRead(context: QueryContext<User>): boolean {
const userAuth = this.getUserAuth();
}